
Rob Wassink is TIBER Test Manager at DNB. When he joined the company more than three years ago, DNB was already doing the TIBER tests for the 'financially critical infrastructure', including the largest banks. This was such a success that the tests have also been done voluntarily at pension funds and insurers since 2019. Wassink calls it "very powerful" to see how open insurers dare to adopt a mutual attitude. "It is not easy to admit that there is a vulnerability in your organisation. Yet insurers dare to share that in a trusted group. Fortunately, because insurers can learn so much from each other."
In the summer of 2022, DNB reassessed the threat landscape for Dutch financial institutions. Members of the Association were then able to request which cyber risks they should take into account. Insurers that have not yet done so can still receive the so-called Financial Threat Landscape for the Netherlands , via j.schaffers@verzekeraars.nl.
Wassink knows what he is talking about. Before joining DNB in 2019, he worked in the insurance industry for a long time. "I have learned a lot in recent years. My focus was more on risk-based defence. This produces a completely different result than when you look at the cyber threat and analyse possible attack scenarios, as we do in the TIBER program. With our TIBER Cyber Team, we pay attention to hacker groups from organised crime, but also to groups that work for foreign governments and pose a threat to Dutch society. What kind of data are they looking for? How do they attack? And what are hidden treasures for hackers?"
According to Wassink, insurers have been increasingly aligning their security measures with the threat from various hacker groups in recent years. "In the TIBER program, we share this threat information, so that we can also strengthen each other in that way."
When asked why DNB is 'interfering' with the cyber resilience of the financial sector, Wassink answers with one word: trust. "DNB considers trust to be of paramount importance. It is essential for financial stability and that is a core task of DNB. That trust is damaged when an insurer is hacked and is therefore out of circulation. Of course, the sector itself takes responsibility for preventing this. We facilitate that cooperation. In this way, we ensure that all tests are carried out at a high level. In addition, we offer a safe environment to share information with each other. And to learn. Together with the financial sector, we are working to stay one step ahead of the hackers."
He gives an example. "Recently there was a major hack at a health insurer in Australia. Those hackers had access to medical data, among other things. They demanded money. When they did not receive that, they published very sensitive data from which it could be deduced who had undergone which procedures. That is of course downright shocking."
Wassink calls it "good that insurers are increasingly aware of what sensitive data they have in their hands, so that they also know how vulnerable they are. This means that they can really do something to become more resilient. Just being compliant with rules is not enough. You also have to test your measures and practice what you can do if things do go wrong."
"Together with the financial sector, we try to stay one step ahead of the hackers"

The team Wassink is part of helps the sector with those tests and exercises. It consists of only nine people. "That is still possible, because we work closely with experts from the institutions."
In fact, DNB's TIBER program works so well that the European Central Bank adopted the method of testing in 2018. "At the moment, sixteen central banks in Europe are working with TIBER tests and have a team just like ours. These TIBER Cyber Teams (TCTs) work together and supervise the tests in their own country. In these threat-based red team tests, three attack scenarios are simulated, which provide valuable insights that are also shared among themselves."
He emphasises it. "We are not part of DNB supervision. For insurers, we are therefore often the odd one out. DNB, no supervision. It is necessary to create a trusted environment where information can be shared. We also do not share test results with the regulator. The institution does this itself, after the test. After all, it is their data. To guarantee confidentiality, we work in a separate room in the DNB building and always use code names for the institutions. Think of Golden Goat or Crazy Canary."
Wassink says he is 'not a techie pur sang and not a hacker either'. "We don't hack ourselves. The institution has this done by ethical hackers who are hired from a security provider. DNB's TIBER framework is the guideline that enables us to carry out these types of tests with the highest quality. With our team, we are on top of it. I make sure that the testing process runs smoothly, while a colleague of mine checks whether the threat situation is appropriate for the institution undergoing the test."
That sounds exciting and to a certain extent it is, says Wassink. "Every TIBER test is like a real attack in the 'live' production environment. If data is 'stolen' during the test, it will come across as lifelike to the attacked institution. Only a handful of people from the company undergoing the test are aware. There is always a board member in that team. He or she is of course aware of the risks, but sometimes only then sees the impact of the dangers that the organisation runs for the first time. And realises where hackers can still get despite all the security measures. That often works as an eye-opener. Suddenly an organisation sees that it has to defend itself very specifically against 'real' attackers. Beautiful, of course. That's exactly what we do it for!"
But testing does not solve everything, Wassink continues. "Sometimes the solution is not as unambiguous as you would like. We recently did a test at a large financial institution. The scenario was a ransomware attack in which all of the company's data was encrypted. 'The hackers' successfully entered and were able to place the ransomware . The 'evil choice' was whether or not to pay. If you pay, you are funding criminals. Not paying means that you may not be able to provide services for a longer period of time. What are you doing? Do you choose principled or pragmatic? In this case, the testing team chose to submit the questions to the administrators involved. They were shown the impact of an attack and how quickly you have to make decisions under pressure. That made an impression. The case has taught us that you want to make these kinds of considerations before the attack. Especially in times of stress and under time pressure, it helps to have a script ready for predictable scenarios."
"We never use the real names of the institutions, but talk about Golden Goat or Crazy Canary"

Wassink is firmly convinced: testing and practising make you better. "We regularly see that after an audit, basic hygiene seems to be in order, but that 'hackers' later run off with the crown jewels in a test. Painful, but also understandable. Basic Hygiene and defending against advanced attacks complement each other. An improvement plan is therefore drawn up after each test."
He makes the comparison with a fire drill. "After such an exercise, everyone knows what to do. A continuous test cycle therefore helps enormously. It keeps people on their toes, without putting too much strain on them. If something happens, everyone knows what to do. And just as important: they have the right mindset and skills."
DNB has been working on the TIBER tests for six years now. Interest from insurers is increasing. "At the moment in the TIBER program, we only have the vital institutions in scope. Both from the banks and from pension funds and insurers. That is nice and logical to start with, but we are now also looking at the ring around these vital institutions. It is important that medium-sized insurers and important suppliers also prepare for a real attack. Because despite all the preparation, it can happen that a real cyber attack on an organisation is successful. Together we can work to minimise the impact," Wassink concludes.
Text: Miranda de Groene - Photography: Ivar Pel
"It is important that medium-sized insurers and important suppliers also prepare for a real attack"
 DNB's TIBER Cyber Team has created a visualisation, a 'discussion board', of the test steps that an organisation can go through itself to prepare for a TIBER test and thus for a real cyber attack. After all, good preparation is half the battle and stands or falls with a good foundation: the security organisation must be in order.
DNB's TIBER Cyber Team has created a visualisation, a 'discussion board', of the test steps that an organisation can go through itself to prepare for a TIBER test and thus for a real cyber attack. After all, good preparation is half the battle and stands or falls with a good foundation: the security organisation must be in order.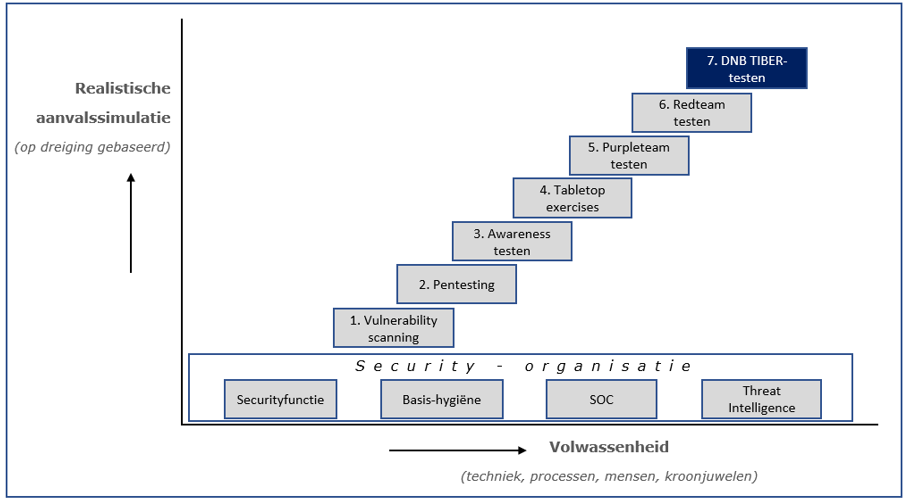
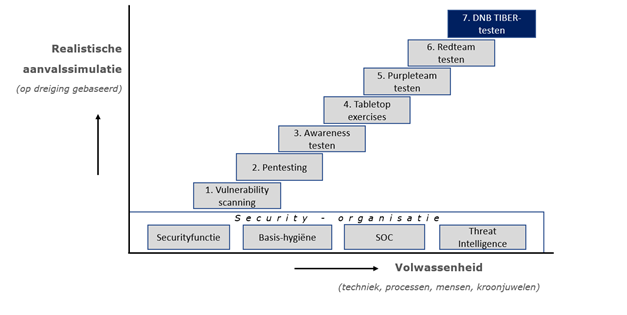
Security organisation
The security organisation is often set up under the direction of the security function, the (chief) information security officer. It starts with basic hygiene, appropriate measures where the security operating centre (SOC) provides 7x24 hour monitoring and effective incident response. Threat intelligence (threat intel) helps the organisation to prevent security incidents. DNB sees an increase in cyber threats while basic hygiene is not always in order.
Security testing
Subsequently, security tests increase the resilience of the security organisation, so that the impact in the event of a real cyber attack must be limited. Each test provides insights into vulnerabilities. These learning points must be addressed. Repeating testing is important, as new vulnerabilities are discovered daily and hackers continue to evolve.
However, security testing is only instructive if the type of test is tailored to the maturity level of the organisation.
The 'talking board' shows that it starts with technical tests, usually on IT infrastructure. The more mature the organisation becomes, the more often entire systems, employees and processes are tested for vulnerabilities. Testing based on relevant cyber threats makes the test even more realistic.
The different types of security tests:
1. Vulnerability scanning: everything that deviates makes it vulnerable. There are tools that (automatically) scan all components in the network and check whether they still have the required technical configuration.
2. Penetration testing: the word says it all, pen testing goes a step deeper than vulnerability scanning. But they are often carried out with a limited scope of IT systems, precisely to find out what a hacker can do with that scope.
3. Awareness tests: make employees and management aware of the practices of hackers. Let them experience how they can give access to important systems and information. This increases safety awareness in the organisation.
4. Tabletop exercises: a crisis exercise for management trains the organisation in managing a crisis. In this step, the skills of management are tested at strategic, tactical and operational levels.
5. Purpleteam testing: blue (defending organisation) with red (the attacker) makes purple (purple). The red team shows how a cyber attack can be carried out, the blue team watches.
6. Redteam testing: This tests the security of the entire organisation. The premises, the processes, the technology and the employees must form a strong front against all types of attacks.
7. TIBER: this type of red team testing based on cyber threats is supervised by the DNB team. Test results are not shared with the regulator and vital institutions participate on a voluntary basis.
More info? Watch TIBER: together against cybercrime.
Questions and/or comments? Then mail to Rob Wassink.